How and why did I virtualize my home perimeter firewall?
Why?
- Cost. It’s really cheap and I get a lot more extra functionality virtualizing everything compared to buying a separate device to use as a firewall.
- Ease of Management. I can migrate and manage the firewall without needing to physically touch the hardware.
- Because it’s really cool. I really like the idea of having everything running in one self-contained physical machine (as much as I realize it’s a massive single point of failure).
Disclaimer : This is not how you should build a production or enterprise server or network environment. At the end of the day, it’s my own home network and if it goes down I’ll have fun fixing it. My ISP also has more outages than I do.
I am using Proxmox VE for the hypervisor, pfSense Community for the firewall, Ubiquity Unifi for the access points, and OpenMediaVault for my NAS.
Hypervisor Configuration
For the hypervisor, I chose a Beelink SEI11 Mini PC, which came with an 11th gen i5, 16 GB DDR4, and a 500 GB NVME M.2. This has a very small footprint and I was able to buy it at a pretty low price. I replaced the RAM with 64 GB DDR4, and installed additional storage. This also came with Windows 11 Pro and I was able to grab the license off the system before reformatting and installing Proxmox VE.
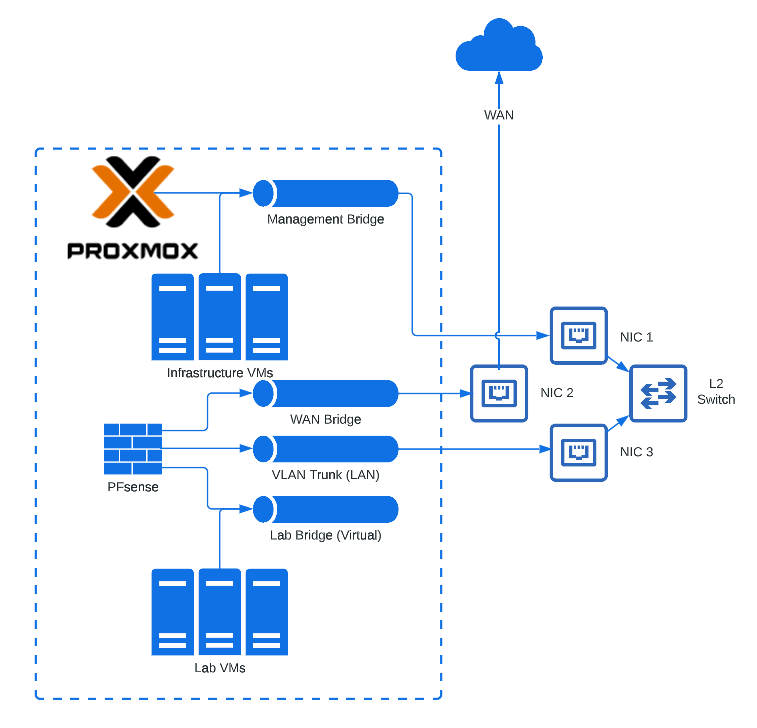
The mini PC did not come with multiple NICs, so I added several ethernet to USB adatpers to provide additional physical NICs for the firewall (janky, I know, but they are gigabit 🙂). The reason for having separate physical NICs is because I wanted to give the firewall an exclusive physical connection for both WAN and vLAN trunks separate from the hypervisor’s management interface. I also ran into problems where the firewall’s gateway wasn’t being recognized by the hypervisor, so it was just easier to have the hypervisor connect to the firewall physically and not “know” it was hosting it.
Proxmox VE on the Beelink has three physical connections.
- The primary physical connection is used by the hypervisor itself for management access, and shared via bridge with guest VMs which need to be on the management network (I could also use the VLAN Trunk interface used as LAN by Proxmox and add a vLAN tag to any VMs in Proxmox). This is plugged into the L2 switch.
- The secondary physical connection is only used by my PFSense VM for WAN (hypervisor has no IP configured). This is plugged directly into my modem’s WAN port.
- The third physical connection is a vLAN aware trunk. The PFSense VM is not configured with a tag on this interface since it is vLAN aware. This is plugged into the L2 switch.
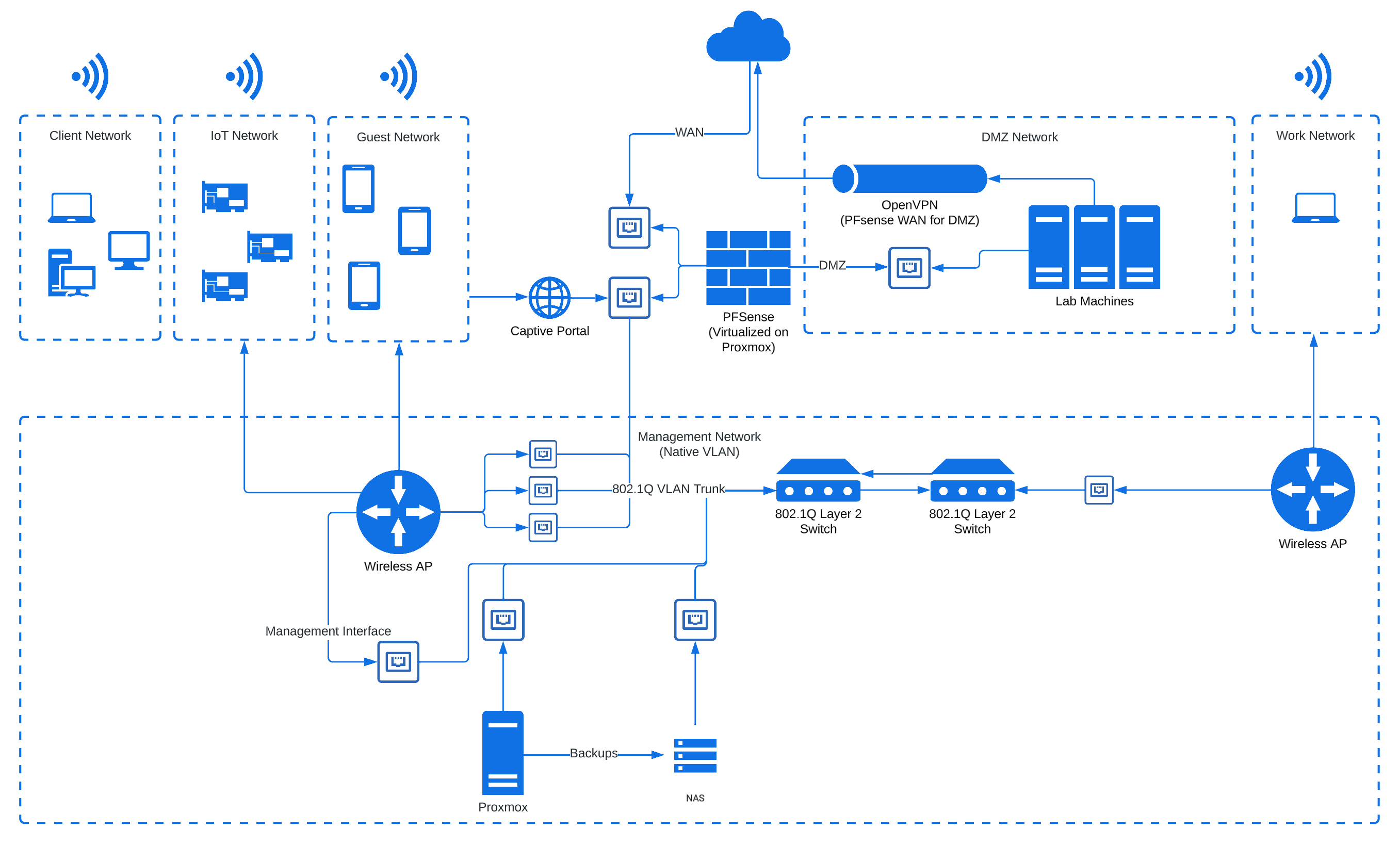
The Network Infrastructure
TP-link layer 2 managed switches which are vLAN capable provide (good enough) separation between networks and allow for native vLANs.
Ubiquity APs with a virtualized controller provide vlan capable wireless network access, and handle roaming.
Network Monitoring, IDS/IPS
Dedicated Email Relay server (postfix) forwards unauthenticated and unencrypted internal email alerts using TLS to AWS SES for delivery. My other infrastructure can send emails through this server without needing to necessarily worry about encryption or authentication. No data sent this way is very sensitive or valuable. Using SES means I don’t have to expose my public IP in any kind of DNS records.
Greenbone OpenVAS performs scheduled network scans of any services on my network.
Opencanary honeypot will immediately notify me of any interaction with it (including port scans or even just TCP connections). I use the firewall to forward ports and publish the server to all of my internal networks via virtual IPs (I only need one honeypot server to cover as many IPs as I want).
Arpwatch on PFSense will notify me of any network changes such as a new device initiating connections.
Wazuh is the SIEM / XDR platform of choice since it’s FOSS.
The Lab Network
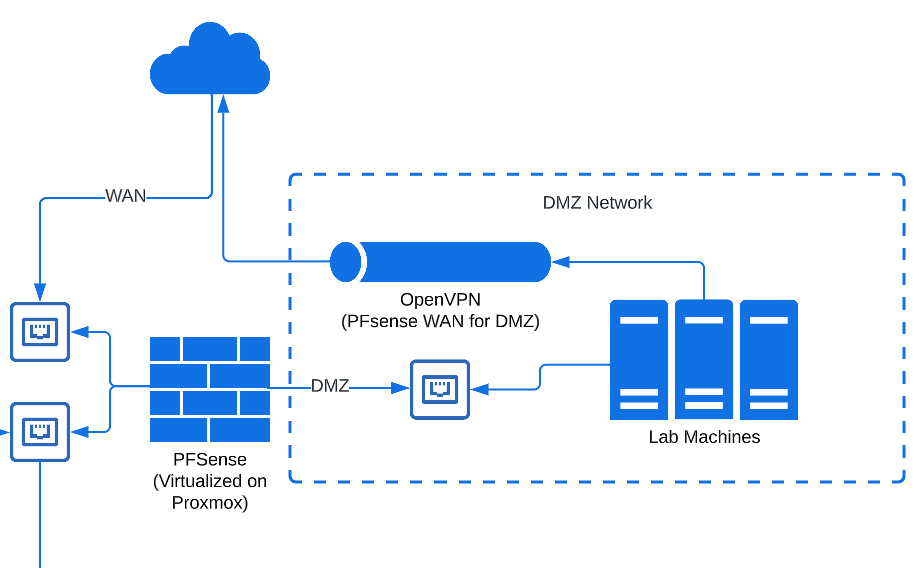
I use my lab for penetration testing practice, security research, and other things I don’t want exposed to my home network. The Lab has its own network which is isolated from the rest of my home network. Even though it does not have any port forwarding to it, I consider the network a DMZ and treat all devices on it as publicly accessible. As such, I apply appropriate security controls and hardening to compensate.
Beyond isolating the vLAN so that it cannot talk to other internal networks, and regularly verifying this through port scanning, the WAN interface for this vLAN uses OpenVPN to avoid IP leaks for OpSec purposes (I may detonate potential malware or open untrusted URLs for security research, and I don’t want my public IP leaking to malware authors or threat actors–anything to avoid being a target of zero-day attacks or DDoS).
I currently have a hardened Parrot Linux instance which I access using SPICE through the hypervisor, that way I don’t need to expose VNC or SSH or even have any network connections to the machine. From the VM’s perspective, I’m accessing it physically. Out of an abundance of caution and paranoia I treat this instance as if it were compromised and don’t use it to process any sensitive information (even though I have ways of confirming it’s clean). As such, this VM will live on this network and never migrate to another network.
Wireless Networks
I have four separate wireless networks:
- Client network supports normal personal devices (laptops, phones, tablets, etc) and has no management access by default.
- IoT network supports “IoT” devices, which I classify as anything that requires a WiFi connection that isn’t a smartphone, tablet, laptop, or other personal computing device (cameras, alarm systems, smart speakers, robot vacuums, etc). This network is isolated with some exceptions.
- The guest network is restricted such that it can only connect to the internet. AP Isolation prevents devices on this network from communicating with other wireless clients and the network has a captive portal which requires a valid voucher before any internet access is allowed (PFsense feature). There’s also a clickwrap Terms of Service agreement that forces each connected device owner to consent to vulnerability scans and network monitoring and sets a warning about unauthorized access (CFAA).
- The work network is for any devices which I do not own (generally work devices). Devices on this network may have agents installed which allow remote access by third parties, and I do not want to include them in vulnerability scans since I do not want to collect or generate potentially sensitive data about devices not under my control.
What’s next?
I am planning to move the majority of the services on my network over to a zero trust architecture using an overlay network with edge access. The isolation I get between networks from my vlans isn’t enough for me to feel completely comfortable exposing services to the internet.